Google to mark non-HTTPS sites as ‘not secure’ from July
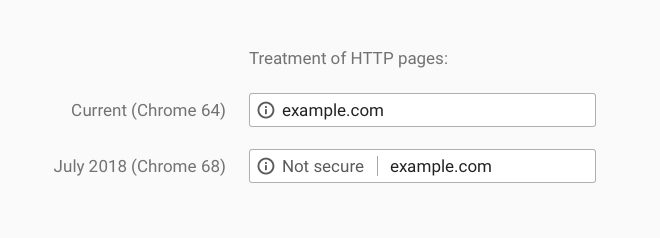
It has been announced on the Google Security Blog that Chrome will mark all HTTP sites as “not secure” from July, with the change debuting on Chrome 68.
For many years now the search engine has been ushering webmasters towards HTTPS encryption, including in early 2017, when it began marking HTTP pages as “Not Secure” if they had password or credit card fields.
Google also marked all HTTP pages opened in a private browsing window as “Not Secure” when it published Chrome 62 in October of the same year.
Since pushing the transition, the search engine has reported that over 68 per cent of Chrome traffic on Android and Windows is protected, alongside 78 per cent on Chrome OS and Mac.
A total of 81 out of the top 100 websites on the internet now use HTTPS as default.
Emily Schechter, the Chrome Security Product Manager said, “based on the awesome rate that sites have been migrating to HTTPS and the strong trajectory through this year” and that “we think that in July the balance will be tipped enough so that we can mark all HTTP sites.”
For those not in the know, HTTPS encryption works by protecting the channel between a browser and a website, so that third parties are unable to tamper with traffic or view what a user might be doing.
This is particularly important when websites happen to take financial information and other transactions.
Without HTTP it is possible for a hacker to access a user’s router or ISP and intercept critical information sent to websites.
It’s also possible for hackers to inject malware into legitimate web pages.
Both Chrome and other organisations are offering services to help websites adopt. In the same security post Google has pointed towards its Lighthouse tool, which includes a host of features for migrating a website to HTTPS.
Of course, Chrome is not the only web browser to punish HTTP websites, as in December 2017, Mozilla engineers began working on the Firefox browser so that it too would mark sites as “Not Secure” if they had not moved across to HTTPS.
Although the company is yet to announce a deadline for when it planned to activate the new policy, it did state in January that all web-based features shipped with Firefox must be served over a secure HTTPS connection.
Anne van Kesteren, a Mozilla engineer said, “effective immediately, all new features that are web-exposed are to be restricted to secure contexts.”
This means that if new standards or features carry out communications between a browser and an external server, they must be carried out using HTTPS, or the standard or feature simply would not work.
This does not affect currently existing standards or features.