Facebook: Please fix this security loophole before it’s too late
A few months ago, I discovered a security loophole in Facebook that allows hackers to decrypt and sniff out Facebook user IDs using one of Facebook’s APIs in bulk – therefore allowing them to gather millions of users’ personal data (name, telephone number, location, images, and more). This post is an attempt to catch Facebook’s attention to get this issue fixed.
Through this, a hacker can then communicate with Facebook’s GraphQL to get as many details as possible, by passing the hashed ID.
By using a script, an entire country’s (I tested with the US, the UK and Canada) possible number combinations can be run through these URLs, and if a number is associated with a Facebook account, it can then be associated with a name and further details (images, and so on).
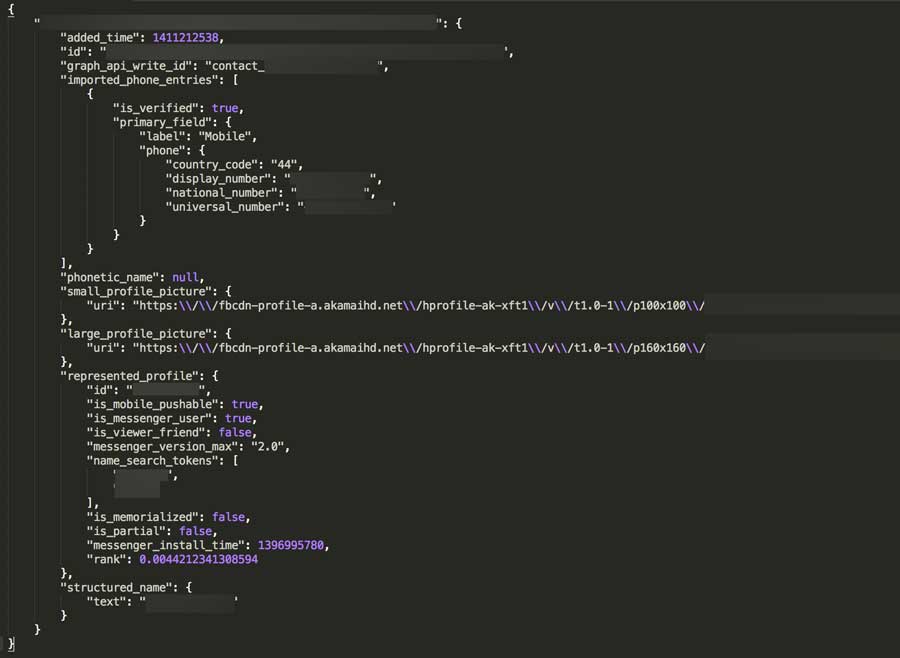
This could be a huge phishing problem if no limit is created, and the loophole is discovered by the wrong person. The communication with those APIs needs to be pre-encrypted and/or other measures need to be taken before this loophole is discovered by someone who could do harm.
How I discovered this security loophole
Perhaps the most worrying aspect of discovering this issue is that it happened entirely by mistake – I wasn’t even searching for flaws in Facebook’s security when I came across it.
What does this issue mean for Facebook users?
Unfortunately, for the 1.44 billion people currently using Facebook, this means that sophisticated hackers and black market sellers can access names and mobile phone numbers in as little as an hour through reverse engineering – at a time when an entire identity can be sold for as little as $5.
What can be done about this issue?
The good news is that Facebook should be able to fix the problem by limiting the requests from a single user, and detecting patterns, before moving on to pre-encrypting all of it’s data.
For those of you who are wondering why I haven’t notified Facebook about the issue, the truth is that I have – back in April (2015).
Although I did receive a reply, initially the engineer I was in contact with was unable to reproduce the issue himself, and therefore failed to understand the technical details of how it should be fixed.
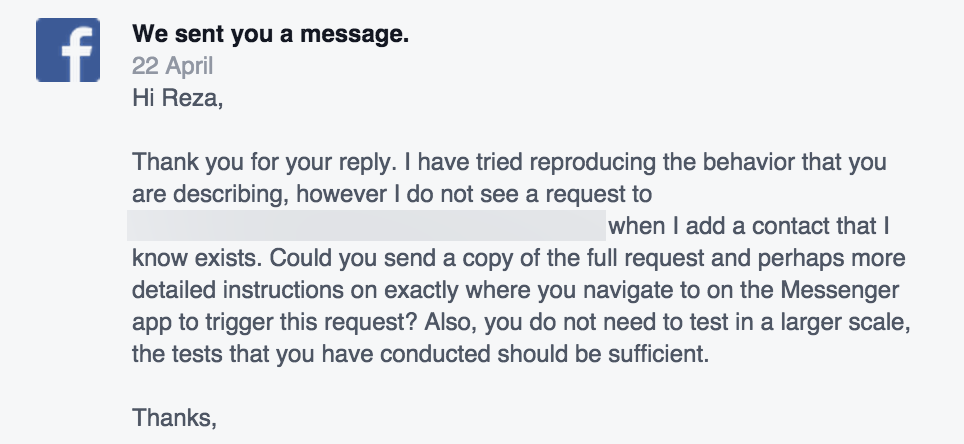
After a couple of months of waiting, I initially thought someone else will look into it and fix it but I heard nothing, so I raised the flag with them again. They finally came back to me and told me that this is not a big issue – they have set limits and I should not worry about this problem. But frankly, I am very worried.
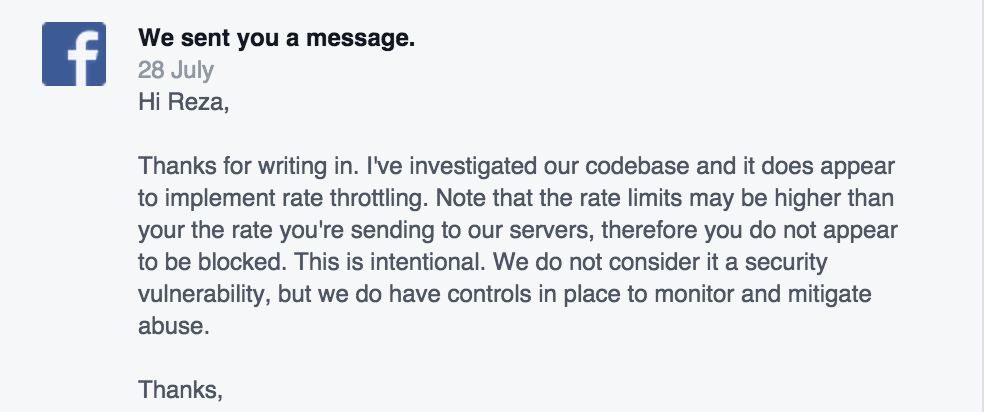
What next?
For now, this is as much detail I can show, but I will update this post if further actions are taken. Hopefully this will be shared enough that Facebook will take notice, get in touch with us, and get this security issue fixed once and for all.
—
Are you currently looking for an experienced technical SEO Consultant to help you with your SEO audit? SALT.agency work with companies around the world from our London & Leeds offices.
You are in the right place. Speak to us and see how we can help you and your SEO project.